Now all websites on the server use some kind of database to store data related to the website and website users, for most of the website they use SQL database which stores data in relational database format. The main objective of using a database for the website, so the dynamic webpages could be formed, on which for each webpage of a website we do not have to create separate HTML pages instead using a single or few HTML webpages we can display various information according to the user need. In dynamic webpages, we can grab data from the database using some backend technology and put that data into the webpage, like this using a single HTML page we can show different data content to the user.
When the concept of Database brought to the web it drastically changed the future of the web and brought many opportunities for the web-developers, but at the same time, it also brought some threats like SQL injection attack.
Here in this article, we will discuss what is an SQL injection attack, how it can be prevented and why this is considered as one the extreme threat to websites.
What is an SQL Injection?
SQL stands for Structured Query Language and it is the most used Database System. There are many famous SQL systems such as MySQL, Microsoft SQL Server, Oracle Database, IBM Informix, and PostgreSQL.
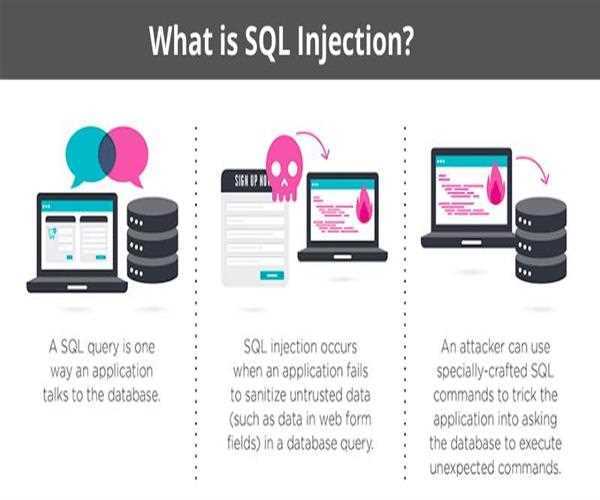
SQL Injection (SQLi) is a kind of attack done by the hacker or website attacker in which a malicious instruction passed through some input format to perform the malicious task. We all know every website use some kind of database system to store data and most of the website on the server using SQL database because it is one of the popular database systems. Every web-page contain some kind of forms such as search form, login form, sign up form, text form, comment form, etc. the main purpose of these forms to collect data from user entry, then that data processed by the backend technology and send to the database system so it could be saved, what if instead of data, user writes an instruction, then the database system would read and execute that statement, rather than saving it as a data this is one of the major Vulnerability of SQL database systems. Forms do not know whether the entered details are information or instruction, it’s work to collect text from the user and send it to the back-end, and at the backend, the Database system takes care of everything.
The attacker takes advantage of this vulnerability of SQL and bypasses the application security measures. This vulnerability of SQL helps attacked to go around the authentication and authorization of any web page or web application, not only this attacker can also retrieve any kind of data by entering any simple instructions. The attacker can inject, modify and even delete all the SQL data of the website.
If any website, use SQL database for webpage or web application so it has some possibility of SQL injection vulnerability. Attackers may use the SQLi to get unauthorised access to the website sensitive data such as customer details, customer credit or debit card details, customer passwords, etc. That’s why SQL injection considered as one of the major threat to the web-development.
Example of SQL Injection:
user = request.POST['username'];
pass = request.POST['password'];
query = "SELECT * FROM users WHERE uname='"user"' AND upass="pass";
k = db.execute(query)
if k == None:
return “Log in unsuccessful”
else:
return “login Successful”
This code is supposed to check the user entered username and password from the database. This could be a simple log in logic.
Here if the user enters the correct detail which matches the database then the login would perform successfully or else it would be an unsuccessful login.
SQLi injection in the code:
If the attacker fills the login form with these details
Username: user
Password: 999; Drop Table
The password just not contain data it also contains an instruction Drop Table, which can delete the complete database.
Types of SQL Injections(SQLi)
An attacker can attack any SQL based webpage in multiple manners. There could be various ways and vulnerability of SQL formation in a webpage which can expose the security of that page. There are some common and famous SQL injections by which an attacker can penetrate through your website security and get to your database.
- Error Based SQLi
- Union-based SQLi
- Blind SQL injection
- Out-of-band Injection
1. Error Based SQL
In this, the attacker used the error message of the database, which mean first the attacker fill input with some random data and if the application or webpage through an error message then the attacker use the error message and evaluate some information from it then attack again. This happens when we create such an application which displays some information about the system in the error message.
2. Union-Based SQLi
In SQL we have a union operator which allow us to execute multiple statements at ones. In Union-Based SQLi the attacker uses this Union operator to inject various SQLi commands. With using the union operator and multiple statements the application may give some crucial data about the system which can be used by the attacker against the system.
3. Blind SQL Injection
It is also known as Inferential SQLi, in this method of injection, attacker randomly tries to attack the database, and try to get some valuable information through the response of the web application or website. The Blind SQL injection is also categorized into two categories:
Boolean-based Blind SQLi: In this method, the attacker sends arbitrary queries and try to get a response in the form of True or False.
Time-Based Blind SQLi: In this method, hacker sends those queries which can take a long time to execute and make the database wait for some specific interval of time.
4. Out-of-band Injection
The attacker uses this method when the webpage or web application server is too slow or the attacker has lost the channel to launch more attacks. In this method attackers used to hack the DNS and HTTP response and try to create an external connection to his server.
SQLi Prevention Techniques
It’s not like that SQL is completely venerable against these SQLi attacks, attackers able to inject malicious SQL instruction in the Database system because of the bad programming at the back-end, if the developer takes care of some precautions and use some solid methodologies and logics the SQL injections attacks could be prevented.
A developer cannot completely remove the SQLi problem, but he can use some precautions and prevention techniques to minimize the risk and he can also increase the complexity of SQLi so the attacker cannot breach the Database system easily.
There are some SQLi prevention techniques which can be used in a web-application to fight against SQLi attacks.
Input Validation: There should be a program for the input validation before sending the data to the database system. The input validation gives the full proof solution against the SQLi attacks.
Form Validation: Many frameworks which are used to build dynamic web application comes with prebuilt form validation tool. The form validation checks the data content and then pass it through the database systems
Web Application Firewall (WAF): This is an application which can be plugged along your web-application and, it can monitor and sanitize the traffic. The firewall helps to detect the SQLi attacker and it can also block the IP address of that attacker.
Regular Updates: The database and the webserver should be updated on a regular interval of time.
Testing: Before releasing the project there should be a full-proof test of the database systems.
Use Placeholders: Placeholders should be used in the statements to perform the SQL queries.
Conclusion
It is impossible to stop the SQLi attacks until or unless we move to another database system such as NoSQL. We can only use some logics and prevention techniques to minimize the risk of injection attacks. The problem is not that much simple, no matter what logic or prevention techniques we use, attackers or hacker will find some contradictory new technique to breach the database. So the best technique to secure your website or web-application, keep updating your page security and use some firewall.



Leave Comment