category
home / developersection / category
How safe is your browser for saving passwords?
In a world where almost everything is online shopping, banking, work, and social media passwords are like the keys to your digital life.
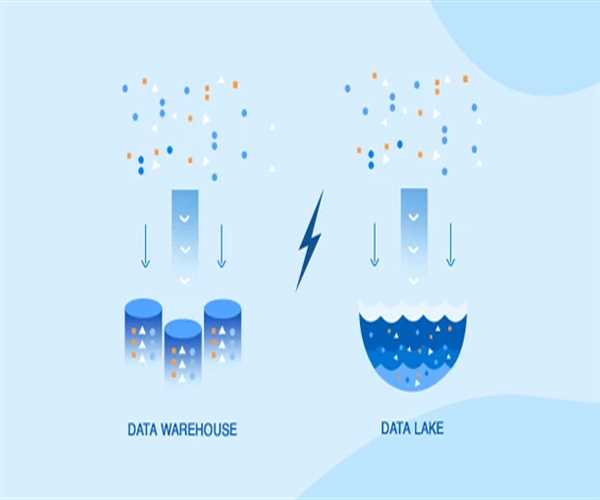
What Is A Data Warehouse, And How Does It Differ From A Data Lake?
This article explores the concept of data warehouses and data lakes, highlighting their differences, use cases, and the advantages of each in the realm of data
Maximizing Value: The Importance of Proper Data Management
Imagine data as the raw material in a craftsman's workshop; to create a masterpiece, you must meticulously shape and refine
2captcha API- How Many Captcha Have You Seen?
If you are constantly facing Captcha while surfing the internet or sending emails or at any moment you can opt for 2 Captcha to solve the Captcha without any ha
Network monitoring best practices
We recommend that you install a Continuous Network Monitoring service to provide better network visibility and facilitate maintenance and troubleshooting.
The most fun technology podcast ever created
we’re recapping the week’s biggest tech stories, channeling debate came to figure out which video game console reigns supreme, proposing solutions to the tweet-editing conundrum, and taking out biggest swing at some tricky tech trivia.
Top 3 Dropbox Alternatives for Users That Care About Their Privacy
Dropbox has been around for about a decade now, and while it has been a pretty decent option for those who need to back up their desktop and mobile device files, one area that hasn’t been free of controversy has been their security record.
What Does Identity And Access Management Mean?
Identity and access management, often referred to as Identity management can be regarded as a framework of several policies and technologies deployed to ensure that the proper individuals within an organization or enterprise, have appropriate access
How Can We Find Complete Internet Security
Internet security is a branch of computer safety which comprises numerous security features exercised for ensuring the security of transactions accomplished online.
Protect all your digital space with McAfee Online backup
Protect all your digital space with McAfee Online backup.
What is Hard Drive Data Recovery
Data failure occurs without notice, often and can paralyze your laptop.
Skills That Are Essential For A Data Scientist
Want to learn Data Science Course and Data Analytics Course in Delhi.