category
home / developersection / category
The Future of Access: Beyond Keys and Cards
For a long time, physical keys and access cards were the only ways to keep things safe
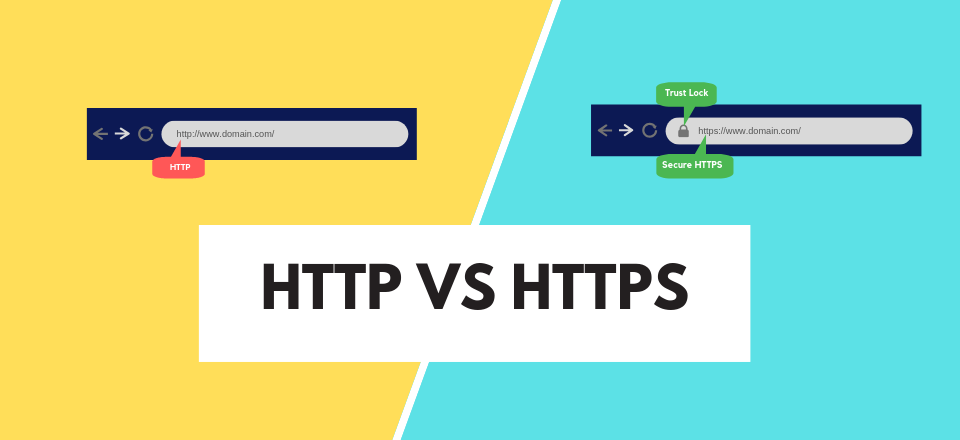
Explaining The Difference In HTTP And HTTPS, Does It Matter For Website Security?
Explore the fundamental differences between HTTP and HTTPS and understand why HTTPS is essential for securing websites.
Enhancing Application Security With OAuth 2.0
This article explores key OAuth 2.0 components, flows, best practices, and practical tips to help developers build secure applications and protect users' inform
Security Benefits Of eSIMs Over SIM Cards
A shift from the traditional capability of physical SIM cards to eSIMs is disrupting the mobile security industry.
How can hackers crack weak passwords? How to prevent hacking?
Learn How can hackers crack weak passwords? How to prevent hacking from this article
What are the hidden dangers of biometric authentication devices?
Learn What are the hidden dangers of biometric authentication devices from this article
Website Security Matters a Lot; How to Do It in 10 Ways
Learn about the Website Security Matters a Lot; How to Do It in 10 Ways in this article
Fortifying Authentication: Securely Encrypting and Protecting Biometric Data in Modern Systems
Learn Fortifying Authentication: Securely Encrypting and Protecting Biometric Data in Modern Systems in this article
Runtime Analyzers and Sanitizers: Identifying Security Issues Effectively
Learn Runtime Analyzers and Sanitizers: Identifying Security Issues Effectively in this article
HSTS and Web Security: Understanding its Key Role
Learn HSTS and Web Security: Understanding its Key Role in this article
Comparing Transport Layer Security (TLS) and Secure Sockets Layer (SSL) Protocols
Learn Comparing Transport Layer Security (TLS) and Secure Sockets Layer (SSL) Protocols: Understanding the Differences in this article
10 Tips for OT Security for Small and Medium-Sized Enterprises (SMEs)
Small and medium-sized businesses (SMEs) can improve their OT security by doing regular risk assessments, training their employees, segmenting their networks.