tag
home / developersection / tag
Remember: There Is No Privacy Online!!!
Research produced by the University of Surrey, Australia released the interesting results of a survey about how respondents viewed privacy online.
Open source Blockchain Platforms for creating unstoppable application
Blockchain works by keeping records of the history of transactions or asset transfers in the form of blocks. Thus, to develop a smart mobile Blockchain app, one needs to use a transaction and ledger model.
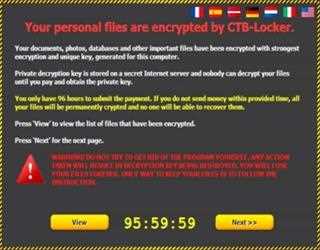
Malware, ransom-ware and spyware and its effects
These three cyber-attacks are the most common and you would have been hearing about these for a long period of time. Malware ransomware and spyware, each of these attacks have a different aim which destroys and de-functions our systems.
What Are The Potential Dangers Of Quantum Computing?
The development of quantum computers may create serious cyber-security threats. The NSA has recently released statements expressing their concern over the potential of quantum computing to foil the cryptography protecting all data to date.
How to Use Honeypots as a Security Measure
Honeypots, as the literal term suggests, are systems set up for luring an attacker into committing an offence in a controlled environment. Honeypots are an important part of the security infrastructure....
How can Blockchain Revolutionize Mobile App Security?
Have you heard of Blockchain? That's already an obsolete question for many of us who closely followed the way data-centric security measures have evolved in the past few years.
India And Pakistan Hit by Spy Malware: Symantec
The detailed report on the cyber spying comes at a time of heightened tensions in the region. India's military has raised operational readiness along its border with China following a face-off in Bhutan near their disputed frontier...
Is Telecom a Bigger Security Threat Than You Realize?
When you think of companies’ security vulnerabilities, what do you think of? If you’re like most people, you likely think of companies’ databases getting hacked by master cyber criminals.
Why You Need Cyber Threat Intelligence
Cyber threat intelligence has become more and more a necessity for every business, no matter how large or small. There are a number of different methods you can implement in order to combat cyber threats, including cyber intelligence.
How to buy and sell bitcoins? Are bitcoins legal in India?
In just one year, the value of bitcoin got increased up to 300 per cent, indicating that it could stand as a well a kind of investment you may be looking for.
Could Cyber Attacks Destroy the Digital World?
Nowadays, there are very few things left that we cannot do online.
Data breaches could cost Indian firms more this year: IBM
Tech giant IBM said in a report that Indian companies could lose Rs.11 crore to data breaches this year that is up 12.3 per cent from last year. We can describe a breach as an event in which an individual's name and a medical/financial record...