category
home / developersection / category
The benefits of using solar energy
If the power plants are spread out the grids could be prone to black outs. If the grid has higher penetration in terms of solar energy then hundreds of solar energy production centres that could be spread out. In case of overload this improves the s
CURSOR AND TRIGGER IN SQL SERVER
The cursor is in SQL a temporary work area created in the system memory when a SQL statement is executed.
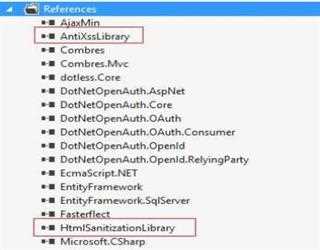
Cross-Site Script (XSS) Prevention
Cross-site Scripting is a vulnerability, that’s typically found in web application. XSS enable attackers to inject malicious line of code like script into web pages.
The Low Down on Gas Powered Scooters
Don't be concerned though, as you've got a lot of alternatives besides driving.
Abstract Methods and Class in C#
Abstract Methods and Class in C# and Similarities with Interface.
Interface in oops
The Interfaces in C# are provided as a replacement of multiple inheritances.
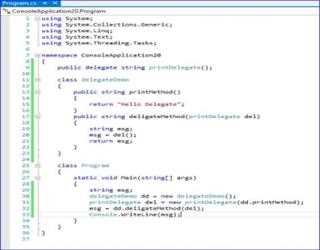
C# - Delegates
A delegate in C# is similar to a function pointer in C or C++. Using a delegate allows the programmer to encapsulate a reference to a method inside a delegate object.
Norton installation stuck on starting? Fix it now
Norton is a top-notch antivirus software package which is suitable for Windows, Android phones as well as iOS devices. It safeguards your devices from viruses, malicious websites and fraudulent links
RDLC report in MVC application
1). How to create a rdlc report in MVC application? 2). Generate RDLC report in asp.net MVC application?
Best Personal Alarm Choices Nowadays
From basic to advanced, you can elect for the system which is suitable for your budget and meets the necessary security demands too
Naming convention or Coding Standard
Naming convention or Coding Standard Programming Standard. Here, I will explain the Naming Convention and Coding Standard of C # for best practice of C # coding.