Introduction
I would like to share the basic of XSS attacks on web applications.
Injection of client side scripts into a website is known as Cross site scripting. These
scripts can be HTML scripts or JavaScript scripts.
There might be various ways to inject script in to browser like attacker can inject
JavaScript from textbox or from query string etc.
Description of attack.
By default XSS attacks are prevented by ASP.net.
I created a sample application to test XSS attack. I followed following steps.
a) Created a ASPX page having code below
Code at page load. |
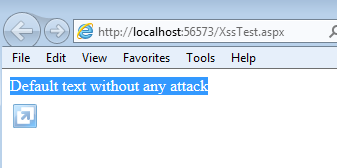
protected void Page_Load(object sender, EventArgs e) { String reqid = Request.QueryString["reqid "] as string; if (id == null) { lblmsg.Text = " Default text without any attack"; } else { lblmsg.Text = reqid; }
|
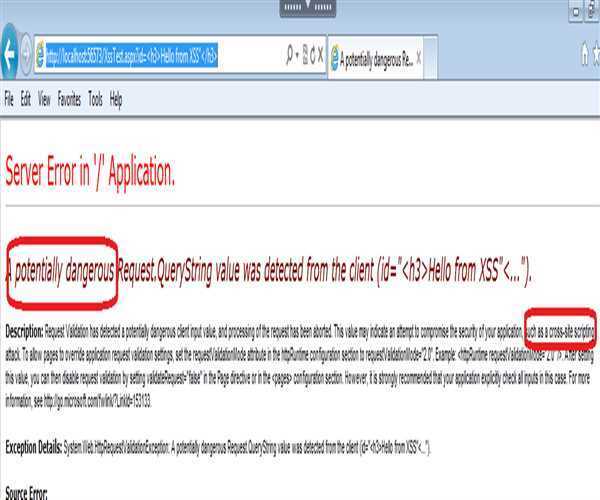
c) Modify the URL to http://localhost:56573/XssTest.aspx?id=<h3>Hello from XSS"
</h3> and paste it to browser.
d) We will get following screen that Request Validation has detected a potentially
dangerous client input value, and processing of the request has been aborted.
e) So by default request validation is implemented by ASP.net. (but we can
disable it with some configuration changes in application )
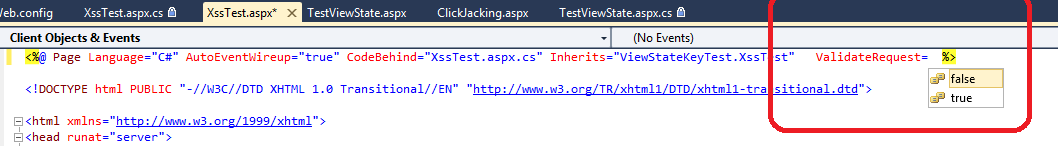
f) Steps to disable the Request validation in ASP.net
Insert following lines in web.config file to enable request validation
o <httpRuntime requestValidationMode="2.0" />
o <pages validateRequest="false"/> // for all pages in applications
o At page level we can use validateRequest = false.
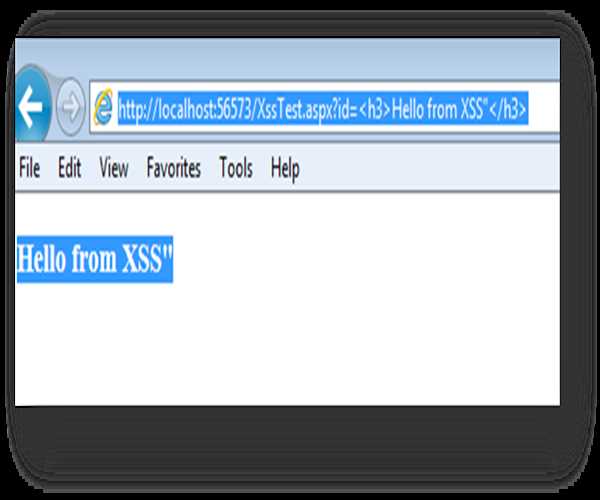
· Modify the URL to http://localhost:56573/XssTest.aspx?id=<h3>Hello from XSS"
</h3> and paste it to browser.
· We will get following screen (now we are able to produce XSS attack)
· If ValidateRequest = false is set at page level then we have to handle these
type of input (script) manually at code level.
Conclusion
By default XSS attacks are prevented by ASP.net so make sure it should be enable
every time.
By default it is enabled by Asp.net.


Leave Comment